Apple is building support for passkeys into the fabric of iOS 17, iPadOS 17 and macOS Sonoma. But what are passkeys and what problems do they solve?
The password problem
People have used passwords and keys as tools to verify identity and manage access. And our reliance on them through the development of technology didn’t finish although we did evolve digital alternatives.
Passwords are widely acknowledged as one of the biggest problems we have with security. Stolen passwords, shared password and weak passwords are the most commonly used tool of cyber criminals. And despite the increasing use of password managers and multi-factor authentication bad guys are still exploiting account takeover to take over systems.
What are passkeys?
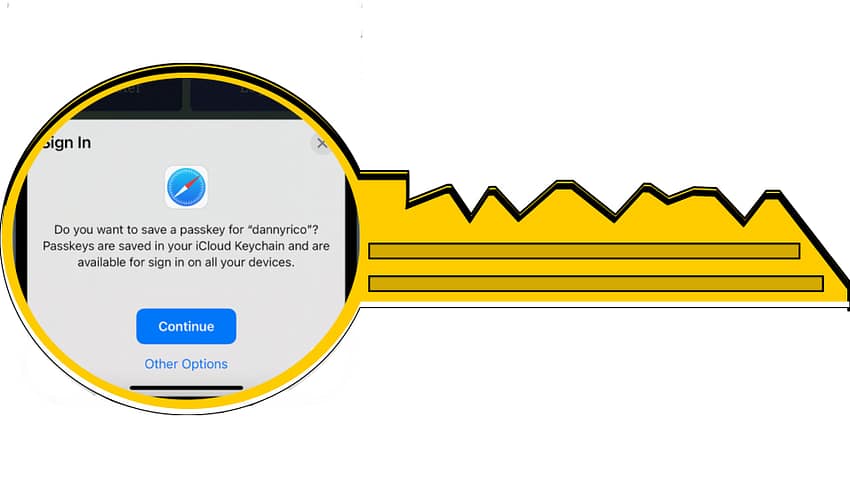
Passkeys are an alternative to passwords. Rather than entering a password, a cryptographic key is sent from the person logging in to the system they are accessing. Rather than typing in a user name and password when signing into website, you can simply scan a fingerprint, face or enter a PIN code for access.
iOS 17, iPadOS 17 and macOS Sonoma are building passkeys into how they work so we can expect their use to become more widespread. Google supports passkeys through the Chrome browser and Android. In short – passkeys are going to become more widely supported. Apple supports passkeys on its websites – it’s what you see when you log in to Apple’s site but are able to use FaceID, TouchID or Apple Watch authentication rather than entering your Apple ID password.
Passkeys are not new – they’ve been around for a while. Devices such as the Ubikey work in a similar way to Apple’s solution which will rely on the T2 chip it has developed to handle cryptographic tasks. And they’re not new to Apple although it will be vastly broadening its support and use in upcomeing
What problem do passkeys solve?
Passkeys create a unique, provate key that’s bound to your devices. The key never leaves the hardware. The website you’re signing into issues a digital challenge which is responded to with your private key on your device. The only response the site seeking authentication gets is a ‘Yes’ or ‘No’.
This makes life much simpler for end users. While tools like multi-factor authentication help, they add complexity to the user experience. And some hackers are finding ways around them, mainly by tricking users into providing those one-time codes created by authenticator apps or sent as text messages. Although more recent attacks have featured criminals stealing cookies – those little computer code snippets that websites leave on our systems so we don’t have to log in every time we visit a site – to bypass multi-factor authentication.
When the passkey is locally stored, which is what Apple does, the only way an attacker can access it is if they steal your device and log into it. If you combine that with a unique and complex password your user accounts become much harder to steal.
And remember, with a passkey, you don’t have to remember the password which means you can have a long and complex password that is extremely hard to guess. And because you never need to key it in to log in, it’s not susceptible to keystroke loggers or man-in-the-middle attacks which steal your passwords as it’s being entered or transmitted.
Passkeys promise to simplify life for users while boosting security and making life harder for criminals. Like any security measure – they aren’t perfect. But no security is. Just as a burglar can break a window even when you lock the doors, it’s likely criminals will find ways to either bypass, break through or trick us to skip past passkeys.
But by making life harder for threat actors, we can make ourselves less of a target.

Anthony is the founder of Australian Apple News. He is a long-time Apple user and former editor of Australian Macworld. He has contributed to many technology magazines and newspapers as well as appearing regularly on radio and occasionally on TV.